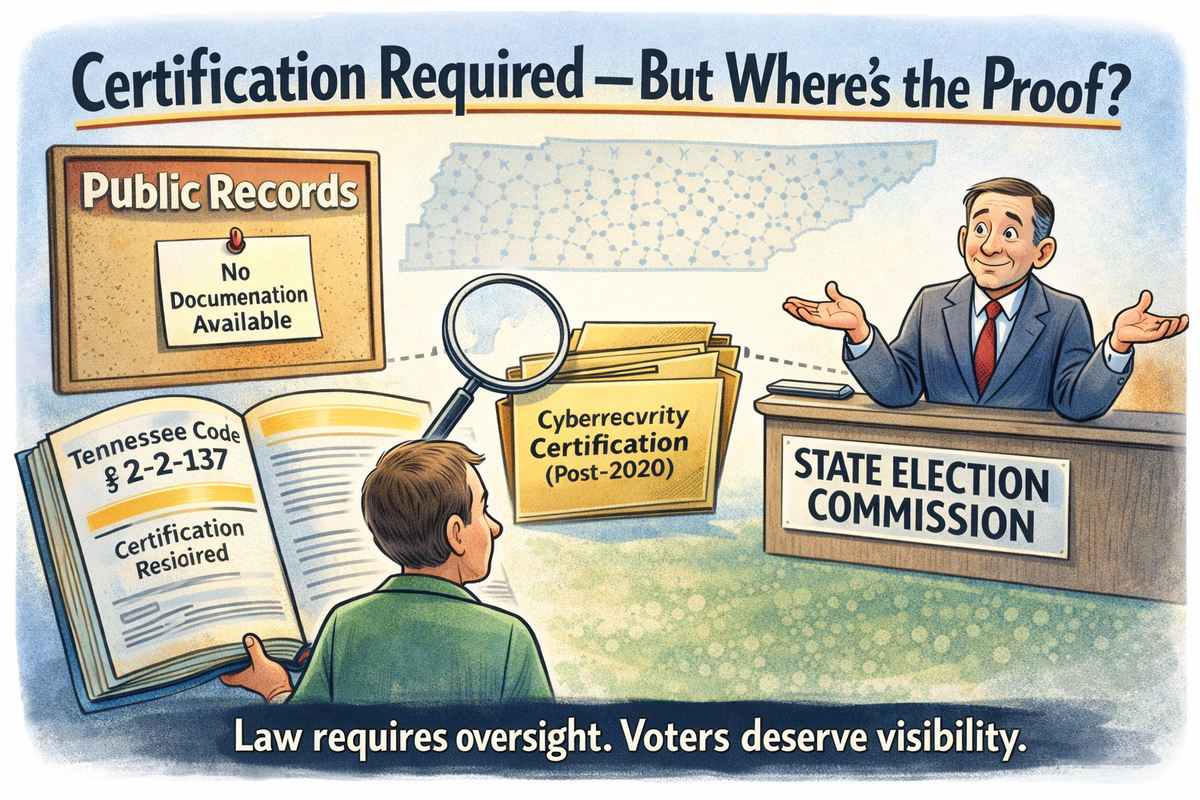
Tennessee law requires voter-registration systems to be examined and certified for cybersecurity, yet voters can’t see proof of how those safeguards are met.
When questions arise about how voter registration systems are managed, election officials often point to state law. Certification requirements, they say, ensure that systems used in Tennessee meet established standards and are safe for use in elections. On paper, those assurances are grounded in statute.
But a closer look at Tennessee law—and the public records associated with it—reveals a gap between what the law requires and what voters are able to independently verify.
Tennessee Code Annotated § 2-2-137 assigns the State Election Commission (SEC) responsibility for examining and certifying voter registration systems used in the state. The statute is not optional. It treats voter registration systems as regulated election infrastructure, subject to oversight before they can be deployed in counties.
In April 2020, the General Assembly amended this statute to explicitly incorporate cybersecurity practices into the certification process. The amendment reflected growing awareness nationwide that digital systems involved in elections—particularly those that store and manage voter data—must be evaluated with modern security threats in mind. The full statutory language is publicly available at this website.
The law is clear in its intent. Certification is meant to ensure systems are examined, approved, and deemed suitable for use. Cybersecurity is no longer implied; it is expressly referenced.
What is less clear is how those requirements are implemented in practice today—and how the public is meant to see that implementation.
Publicly available State Election Commission meeting minutes from January 2015 show that vendors, including Embry Consulting LLC, were examined and approved at that time.
The 2015 approval predates the 2020 statutory amendment addressing cybersecurity by five years. That timing matters, not because earlier certifications were invalid, but because cybersecurity standards evolve rapidly. Practices considered adequate a decade ago may no longer meet current expectations.
Records reviewed for this investigation do not include documentation showing that voter registration systems supported by Embry Consulting were re-certified after the 2020 amendment or assessed specifically against the cybersecurity criteria now referenced in statute.
This does not establish that re-certification did not occur. It establishes that evidence of such review has not been made publicly available.
In many regulatory contexts, certification is not a one-time event. Systems are re-examined periodically to ensure ongoing compliance as laws, technologies, and threat environments change. This is especially true in fields that manage sensitive personal data.
Voter registration databases contain names, addresses, birthdates, and other identifying information. They are updated continuously and accessed by election workers across dozens of jurisdictions. That combination alone places them within a category of systems that typically receive ongoing oversight.
Yet when citizens requested documentation showing how certification requirements are currently satisfied—particularly with respect to cybersecurity—those records were not produced.
Election officials have emphasized that elections are secure and that systems are properly vetted. Those assurances may well be accurate. But without documentation, voters are asked to rely on statements rather than evidence.
Transparency does not require disclosing sensitive technical details. Other jurisdictions routinely publish high-level certification summaries, audit schedules, or confirmation that vendors have met defined security criteria. Such disclosures do not compromise system integrity. They provide a basis for public confidence.
The absence of publicly available certification documentation leaves voters with an incomplete picture. They know the law requires examination and cybersecurity consideration. They do not know how those requirements are fulfilled in practice.
This gap is not merely academic. It intersects directly with the scale of reliance on a single vendor. When one company supports voter registration systems for nearly every county in the state, certification and oversight become even more consequential.
The law anticipates that responsibility. What remains unclear is how its safeguards are demonstrated to the public.
This investigation does not assert that the State Election Commission failed to meet its obligations. It documents that the public cannot independently confirm how those obligations are being met today.
That distinction matters in an environment where election integrity is frequently questioned from all sides. Confidence is strengthened not by asking voters to trust without evidence, but by making oversight visible.
When documentation is not shared, even routine administrative arrangements can appear opaque. Over time, that opacity erodes confidence—not because of proof of failure, but because of the absence of proof.
Tennessee law provides a framework for oversight. The question raised here is whether that framework is transparent enough for the voters it is meant to protect.
Coming Next in the Series
In Part 4, we step back from Tennessee specifically and examine why cybersecurity experts nationwide warn that voter registration databases deserve as much scrutiny as voting machines. Drawing on expert demonstrations, national case studies, and well-documented risks, we explore why voter rolls are often described as the “quiet” but critical layer of election infrastructure.
If you want to support what we do, please consider donating a gift in order to sustain free, independent, and TRULY CONSERVATIVE media that is focused on Middle Tennessee and BEYOND!


Comments ()